Reference
Security
Overview
This document describes the security protocols and practices in use by Pinecone.API keys
Each Pinecone project has one or more API keys. In order to make calls to the Pinecone API, a user must provide a valid API key for the relevant Pinecone project.Role-based access controls (RBAC)
Each Pinecone organization can assign users roles with respect to the organization and projects within the organization. These roles determine what permissions users have to make changes to the organization’s billing, projects, and other users. To learn more, see organization roles.Organization single sign-on (SSO)
SSO allows organizations to manage their teams’ access to Pinecone through their identity management solution. Once your integration is configured, you can require that users from your domain sign in through SSO, and you can specify a default role for teammates when they sign up. Only organizations in the Enterprise dedicated tier can set up SSO. To set up your SSO integration, Contact Pinecone support..End-to-end encryption (E2EE)
Pinecone provides end-to-end encryption for user data, including encryption in transit and at rest.Encryption in transit
Pinecone uses standard protocols to encrypt user data in transit. Clients open HTTPS or gRPC connections to the Pinecone API; the Pinecone API gateway uses gRPC connections to user deployments in the cloud. These HTTPS and gRPC connections use the TLS 1.2 protocol with 256-bit Advanced Encryption Standard (AES-256) encryption. See Fig. 1 below. Figure 1: Pinecone encryption in transit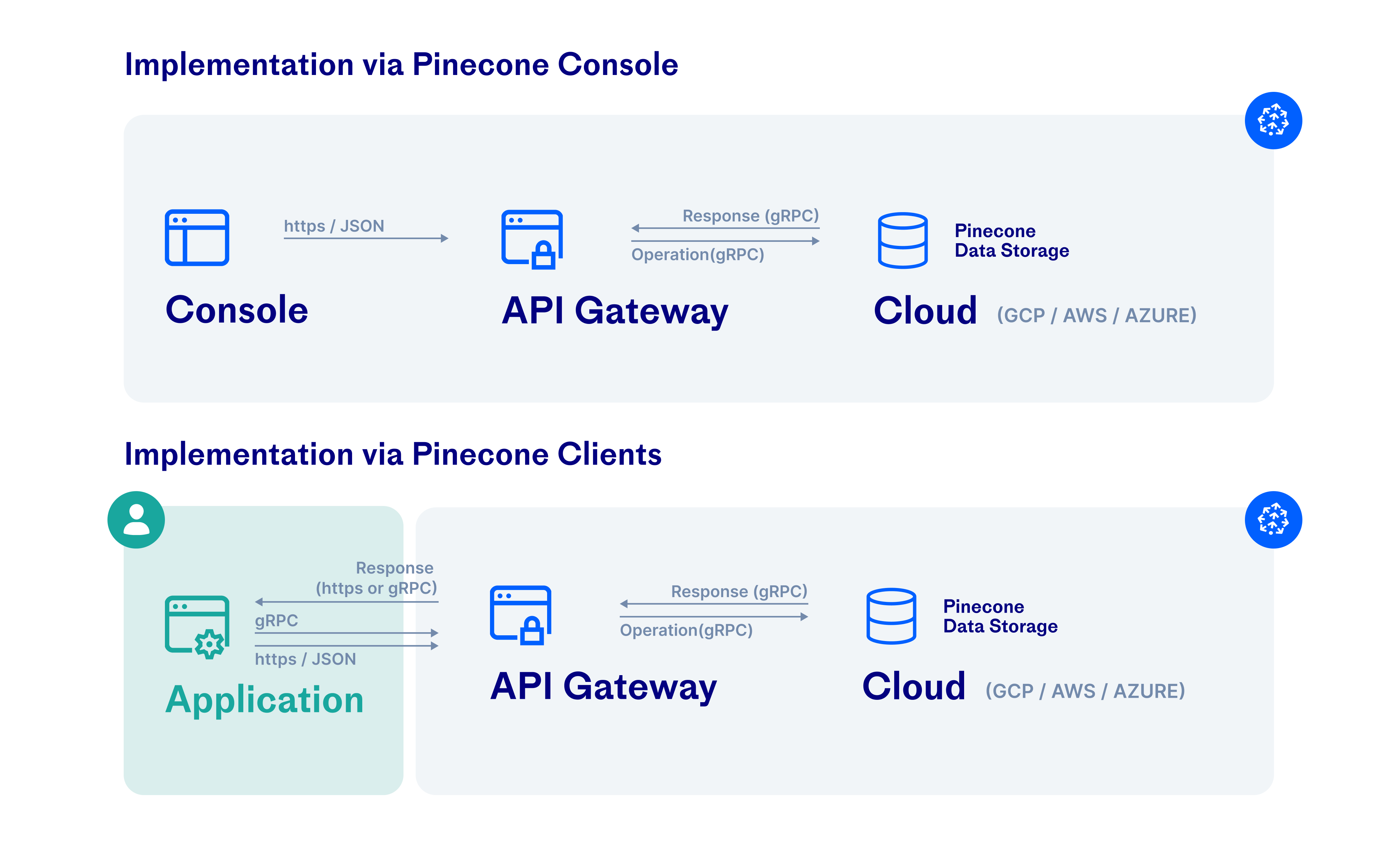 Traffic is also encrypted in transit between the Pinecone backend and cloud infrastructure services, such as S3 and GCS. For more information, see Google Cloud Platform and AWS security documentation.
Traffic is also encrypted in transit between the Pinecone backend and cloud infrastructure services, such as S3 and GCS. For more information, see Google Cloud Platform and AWS security documentation.

